Network Probes Explained: Understanding Port Scans and Ping
Картинки по запросу ping scans
Ping Sweep: Online Penetration Testing Tools | Ethical Hacking Tools
Host Discovery - Nmap
Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Block ping scans (iptables) - LinuxQuestions org
 Discovering hosts with ARP ping scans - Nmap 6: Network Exploration
Discovering hosts with ARP ping scans Ping scans are used by penetration testers and system administrators to determine if hosts are online ARP ping scans
Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Ping scans are used for detecting live hosts in networks Nmap s default ping scan (-sP) uses a TCP ACK and an ICMP echo request to determine if a host is
Network Probes Explained: Understanding Port Scans and Ping
Дек 2000 г -
Block ping scans (iptables) - LinuxQuestions org
I d like to block ping scans from my box I used the following in my firewall rules IPTABLES -A INPUT -p icmp-type echo-request -j DROP I
Ping Sweep: Online Penetration Testing Tools | Ethical Hacking Tools
Ping sweep with Nmap Ping sweep tool online Scan SSL POODLE Scan SSL DROWN Scan Bash Shellshock Scan GHOST Glibc Scan My Scans
Discovering hosts with ARP ping scans - Nmap 6: Network Exploration
Discovering hosts with ARP ping scans Ping scans are used by penetration testers and system administrators to determine if hosts are online ARP ping scans
Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Ping scans are used for detecting live hosts in networks Nmap s default ping scan (-sP) uses a TCP ACK and an ICMP echo request to determine if a host is
Network Probes Explained: Understanding Port Scans and Ping
Дек 2000 г -
Block ping scans (iptables) - LinuxQuestions org
I d like to block ping scans from my box I used the following in my firewall rules IPTABLES -A INPUT -p icmp-type echo-request -j DROP I
Ping Sweep: Online Penetration Testing Tools | Ethical Hacking Tools
Ping sweep with Nmap Ping sweep tool online Scan SSL POODLE Scan SSL DROWN Scan Bash Shellshock Scan GHOST Glibc Scan My Scans
 Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Ping scans are used for detecting live hosts in networks Nmap s default ping scan (-sP) uses a TCP ACK and an ICMP echo request to determine if a host is
Discovering hosts with ARP ping scans - Nmap 6: Network Exploration
Discovering hosts with ARP ping scans Ping scans are used by penetration testers and system administrators to determine if hosts are online ARP ping scans
Картинки по запросу ping scans
Янв 2017 г -
Secrets of Network Cartography - Ping Scan (-sP) - Network Uptime
The ping scan is one of the quickest scans that nmap performs, since no actual ports are queried Unlike a port scan where thousands of packets are transferred
Host Discovery - Nmap
Host discovery is sometimes called ping scan, but it goes well beyond the simple ICMP echo request packets associated with the ubiquitous ping tool Users can
Angry IP Scanner - Pinging
As a rule, if hosts don t respond to pings, they are considered dead and therefore not scanned further This behavior can be changed in the Preferences dialog,
Ping Sweep: Online Penetration Testing Tools | Ethical Hacking Tools
Ping sweep with Nmap Ping sweep tool online Scan SSL POODLE Scan SSL DROWN Scan Bash Shellshock Scan GHOST Glibc Scan My Scans
Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Ping scans are used for detecting live hosts in networks Nmap s default ping scan (-sP) uses a TCP ACK and an ICMP echo request to determine if a host is
Discovering hosts with ARP ping scans - Nmap 6: Network Exploration
Discovering hosts with ARP ping scans Ping scans are used by penetration testers and system administrators to determine if hosts are online ARP ping scans
Картинки по запросу ping scans
Янв 2017 г -
Secrets of Network Cartography - Ping Scan (-sP) - Network Uptime
The ping scan is one of the quickest scans that nmap performs, since no actual ports are queried Unlike a port scan where thousands of packets are transferred
Host Discovery - Nmap
Host discovery is sometimes called ping scan, but it goes well beyond the simple ICMP echo request packets associated with the ubiquitous ping tool Users can
Angry IP Scanner - Pinging
As a rule, if hosts don t respond to pings, they are considered dead and therefore not scanned further This behavior can be changed in the Preferences dialog,
Ping Sweep: Online Penetration Testing Tools | Ethical Hacking Tools
Ping sweep with Nmap Ping sweep tool online Scan SSL POODLE Scan SSL DROWN Scan Bash Shellshock Scan GHOST Glibc Scan My Scans
 Discovering hosts with ARP ping scans - Nmap 6: Network Exploration
Discovering hosts with ARP ping scans Ping scans are used by penetration testers and system administrators to determine if hosts are online ARP ping scans
Block ping scans (iptables) - LinuxQuestions org
I d like to block ping scans from my box I used the following in my firewall rules IPTABLES -A INPUT -p icmp-type echo-request -j DROP I
Angry IP Scanner - Pinging
As a rule, if hosts don t respond to pings, they are considered dead and therefore not scanned further This behavior can be changed in the Preferences dialog,
Network Probes Explained: Understanding Port Scans and Ping
Дек 2000 г -
Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Ping scans are used for detecting live hosts in networks Nmap s default ping scan (-sP) uses a TCP ACK and an ICMP echo request to determine if a host is
Ping Sweep: Online Penetration Testing Tools | Ethical Hacking Tools
Ping sweep with Nmap Ping sweep tool online Scan SSL POODLE Scan SSL DROWN Scan Bash Shellshock Scan GHOST Glibc Scan My Scans
Host Discovery - Nmap
Host discovery is sometimes called ping scan, but it goes well beyond the simple ICMP echo request packets associated with the ubiquitous ping tool Users can
Discovering hosts with ARP ping scans - Nmap 6: Network Exploration
Discovering hosts with ARP ping scans Ping scans are used by penetration testers and system administrators to determine if hosts are online ARP ping scans
Block ping scans (iptables) - LinuxQuestions org
I d like to block ping scans from my box I used the following in my firewall rules IPTABLES -A INPUT -p icmp-type echo-request -j DROP I
Angry IP Scanner - Pinging
As a rule, if hosts don t respond to pings, they are considered dead and therefore not scanned further This behavior can be changed in the Preferences dialog,
Network Probes Explained: Understanding Port Scans and Ping
Дек 2000 г -
Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Ping scans are used for detecting live hosts in networks Nmap s default ping scan (-sP) uses a TCP ACK and an ICMP echo request to determine if a host is
Ping Sweep: Online Penetration Testing Tools | Ethical Hacking Tools
Ping sweep with Nmap Ping sweep tool online Scan SSL POODLE Scan SSL DROWN Scan Bash Shellshock Scan GHOST Glibc Scan My Scans
Host Discovery - Nmap
Host discovery is sometimes called ping scan, but it goes well beyond the simple ICMP echo request packets associated with the ubiquitous ping tool Users can
Block ping scans (iptables) - LinuxQuestions org
I d like to block ping scans from my box I used the following in my firewall rules IPTABLES -A INPUT -p icmp-type echo-request -j DROP I
Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Ping scans are used for detecting live hosts in networks Nmap s default ping scan (-sP) uses a TCP ACK and an ICMP echo request to determine if a host is
Discovering hosts with ARP ping scans - Nmap 6: Network Exploration
Discovering hosts with ARP ping scans Ping scans are used by penetration testers and system administrators to determine if hosts are online ARP ping scans
 Discovering hosts with ARP ping scans - Nmap 6: Network Exploration
Discovering hosts with ARP ping scans Ping scans are used by penetration testers and system administrators to determine if hosts are online ARP ping scans
Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Ping scans are used for detecting live hosts in networks Nmap s default ping scan (-sP) uses a TCP ACK and an ICMP echo request to determine if a host is
Host Discovery - Nmap
Host discovery is sometimes called ping scan, but it goes well beyond the simple ICMP echo request packets associated with the ubiquitous ping tool Users can
Картинки по запросу ping scans
Янв 2017 г -
Angry IP Scanner - Pinging
As a rule, if hosts don t respond to pings, they are considered dead and therefore not scanned further This behavior can be changed in the Preferences dialog,
Discovering hosts with ARP ping scans - Nmap 6: Network Exploration
Discovering hosts with ARP ping scans Ping scans are used by penetration testers and system administrators to determine if hosts are online ARP ping scans
Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Ping scans are used for detecting live hosts in networks Nmap s default ping scan (-sP) uses a TCP ACK and an ICMP echo request to determine if a host is
Host Discovery - Nmap
Host discovery is sometimes called ping scan, but it goes well beyond the simple ICMP echo request packets associated with the ubiquitous ping tool Users can
Картинки по запросу ping scans
Янв 2017 г -
Angry IP Scanner - Pinging
As a rule, if hosts don t respond to pings, they are considered dead and therefore not scanned further This behavior can be changed in the Preferences dialog,
 Картинки по запросу ping scans
Янв 2017 г -
Block ping scans (iptables) - LinuxQuestions org
I d like to block ping scans from my box I used the following in my firewall rules IPTABLES -A INPUT -p icmp-type echo-request -j DROP I
Discovering hosts with ARP ping scans - Nmap 6: Network Exploration
Discovering hosts with ARP ping scans Ping scans are used by penetration testers and system administrators to determine if hosts are online ARP ping scans
Ping Sweep: Online Penetration Testing Tools | Ethical Hacking Tools
Ping sweep with Nmap Ping sweep tool online Scan SSL POODLE Scan SSL DROWN Scan Bash Shellshock Scan GHOST Glibc Scan My Scans
Картинки по запросу ping scans
Янв 2017 г -
Block ping scans (iptables) - LinuxQuestions org
I d like to block ping scans from my box I used the following in my firewall rules IPTABLES -A INPUT -p icmp-type echo-request -j DROP I
Discovering hosts with ARP ping scans - Nmap 6: Network Exploration
Discovering hosts with ARP ping scans Ping scans are used by penetration testers and system administrators to determine if hosts are online ARP ping scans
Ping Sweep: Online Penetration Testing Tools | Ethical Hacking Tools
Ping sweep with Nmap Ping sweep tool online Scan SSL POODLE Scan SSL DROWN Scan Bash Shellshock Scan GHOST Glibc Scan My Scans
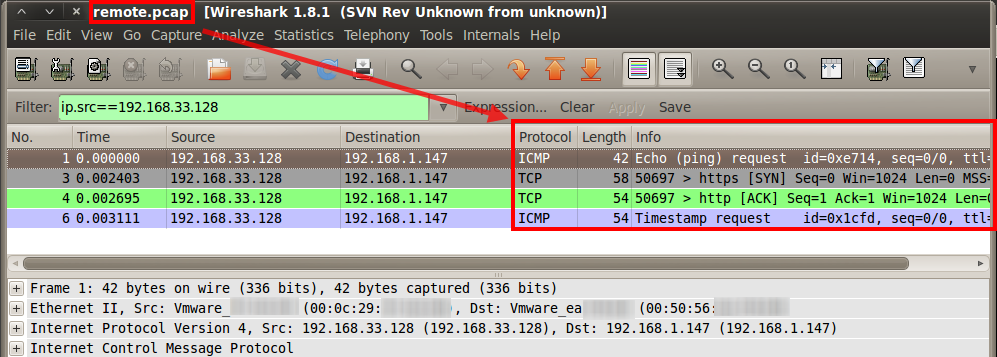 Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Ping scans are used for detecting live hosts in networks Nmap s default ping scan (-sP) uses a TCP ACK and an ICMP echo request to determine if a host is
Картинки по запросу ping scans
Янв 2017 г -
Discovering hosts with ARP ping scans - Nmap 6: Network Exploration
Discovering hosts with ARP ping scans Ping scans are used by penetration testers and system administrators to determine if hosts are online ARP ping scans
Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Ping scans are used for detecting live hosts in networks Nmap s default ping scan (-sP) uses a TCP ACK and an ICMP echo request to determine if a host is
Картинки по запросу ping scans
Янв 2017 г -
Discovering hosts with ARP ping scans - Nmap 6: Network Exploration
Discovering hosts with ARP ping scans Ping scans are used by penetration testers and system administrators to determine if hosts are online ARP ping scans

 Secrets of Network Cartography - Ping Scan (-sP) - Network Uptime
The ping scan is one of the quickest scans that nmap performs, since no actual ports are queried Unlike a port scan where thousands of packets are transferred
Ping Sweep: Online Penetration Testing Tools | Ethical Hacking Tools
Ping sweep with Nmap Ping sweep tool online Scan SSL POODLE Scan SSL DROWN Scan Bash Shellshock Scan GHOST Glibc Scan My Scans
Block ping scans (iptables) - LinuxQuestions org
I d like to block ping scans from my box I used the following in my firewall rules IPTABLES -A INPUT -p icmp-type echo-request -j DROP I
Secrets of Network Cartography - Ping Scan (-sP) - Network Uptime
The ping scan is one of the quickest scans that nmap performs, since no actual ports are queried Unlike a port scan where thousands of packets are transferred
Ping Sweep: Online Penetration Testing Tools | Ethical Hacking Tools
Ping sweep with Nmap Ping sweep tool online Scan SSL POODLE Scan SSL DROWN Scan Bash Shellshock Scan GHOST Glibc Scan My Scans
Block ping scans (iptables) - LinuxQuestions org
I d like to block ping scans from my box I used the following in my firewall rules IPTABLES -A INPUT -p icmp-type echo-request -j DROP I
 Ping Sweep: Online Penetration Testing Tools | Ethical Hacking Tools
Ping sweep with Nmap Ping sweep tool online Scan SSL POODLE Scan SSL DROWN Scan Bash Shellshock Scan GHOST Glibc Scan My Scans
Angry IP Scanner - Pinging
As a rule, if hosts don t respond to pings, they are considered dead and therefore not scanned further This behavior can be changed in the Preferences dialog,
Block ping scans (iptables) - LinuxQuestions org
I d like to block ping scans from my box I used the following in my firewall rules IPTABLES -A INPUT -p icmp-type echo-request -j DROP I
Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Ping scans are used for detecting live hosts in networks Nmap s default ping scan (-sP) uses a TCP ACK and an ICMP echo request to determine if a host is
Ping Sweep: Online Penetration Testing Tools | Ethical Hacking Tools
Ping sweep with Nmap Ping sweep tool online Scan SSL POODLE Scan SSL DROWN Scan Bash Shellshock Scan GHOST Glibc Scan My Scans
Angry IP Scanner - Pinging
As a rule, if hosts don t respond to pings, they are considered dead and therefore not scanned further This behavior can be changed in the Preferences dialog,
Block ping scans (iptables) - LinuxQuestions org
I d like to block ping scans from my box I used the following in my firewall rules IPTABLES -A INPUT -p icmp-type echo-request -j DROP I
Discovering hosts with TCP SYN ping scans - Nmap 6: Network
Ping scans are used for detecting live hosts in networks Nmap s default ping scan (-sP) uses a TCP ACK and an ICMP echo request to determine if a host is